Solving Incapsula & hCaptcha: Complete Guide to Imperva Security
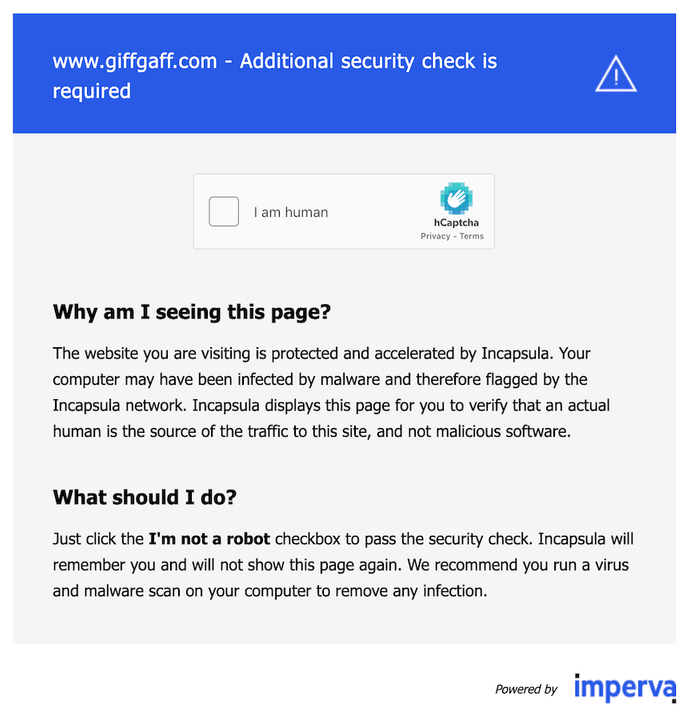
Imperva (formerly known as Incapsula) is a sophisticated cloud-based application delivery service that provides comprehensive web security, DDoS protection, CDN, and load balancing capabilities. When it detects potential automated access, it interrupts browser automation with an interstitial page requiring a security check, typically in the form of an hCaptcha challenge.
Security Mechanisms Deep Dive
Imperva employs a multi-layered approach to detect and prevent automated access:
1. Browser Fingerprinting System
The security system performs extensive environment checks across several categories:
Core Navigator Properties
- User Agent string analysis (
navigator.userAgent) - Webdriver presence detection (
navigator.webdriver) - Browser plugins enumeration (expecting
plugins.length > 0)
Automation Detection
- Selenium IDE Recorder (
window._Selenium_IDE_Recorder) - PhantomJS presence (
window._phantom) - Nightmare.js traces (
window.__nightmare) - General webdriver properties
Device Characteristics
- Screen dimensions (
screen.widthandscreen.height) - Device type classification based on User-Agent patterns:
- Tablet detection:
/(tablet|ipad|playbook|silk)|(android(?!.*mobi))/i - Mobile detection:
/Mobile|Android|iP(hone|od)|IEMobile|BlackBerry|Kindle|Silk-Accelerated|(hpw|web)OS|Opera M(obi|ini)/ - Desktop: fallback when neither tablet nor mobile patterns match
- Tablet detection:
2. Data Processing and Storage
The fingerprint data collection process follows these steps:
- Execution of each environment check
- JSON stringification of results
- Base64 encoding of the JSON string
- Storage in a cookie named
_dcheckwith 24-hour expiration
Technical Note: Failed checks are not discarded but rather recorded with their corresponding error messages, providing additional fingerprinting data.
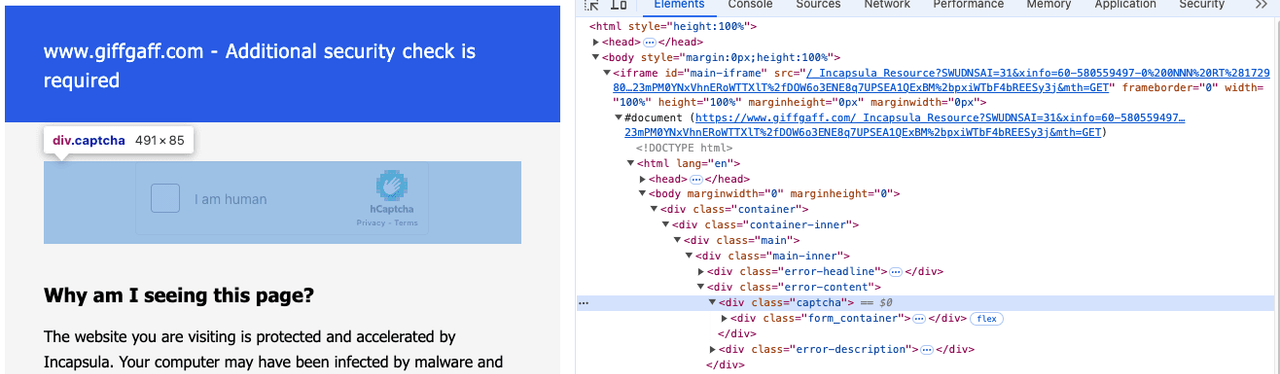
Understanding the Challenge Page
The hCaptcha challenge appears within an iframe when Imperva's security checks detect suspicious patterns. To handle this efficiently, we've developed the open-source library rebrowser-patches which provides full support for working with iframes while maintaining undetectability. The key components involved are:
- The websiteURL and websiteKey parameters
- The generated token and cookie values
- Network protocol indicators
Network Connection Considerations
When dealing with Imperva's security measures, several network-related factors are crucial:
- Request headers must maintain consistency across:
- Language settings
- IP addresses
- Browser versions
- Cookie values
- HTTP/2 protocol is preferred; HTTP/1.1 may trigger additional verification
- TLS fingerprinting is monitored for browser authenticity
- Residential proxies and mobile networks typically face fewer restrictions
Code Analysis and Deobfuscation
When investigating Imperva's initial browser verification script, we encountered heavily obfuscated code that needed to be analyzed. In 2024, we have powerful tools at our disposal that make this task significantly easier - modern Large Language Models (LLMs) like ChatGPT or Claude.
These AI models can quickly deobfuscate complex JavaScript code, providing readable versions in seconds. This capability has revolutionized the analysis of security systems, allowing us to better understand how they operate.
Example of Analysis Process
- Extract the obfuscated verification script
- Pass it through an LLM for deobfuscation
- Analyze the revealed logic and fingerprinting mechanisms
- Identify key detection points like automation flags and environment checks
Pro Tip: When working with obfuscated code, modern LLMs can not only deobfuscate it but also provide insights about the security mechanisms being implemented. This makes it much easier to understand and work with complex security systems.
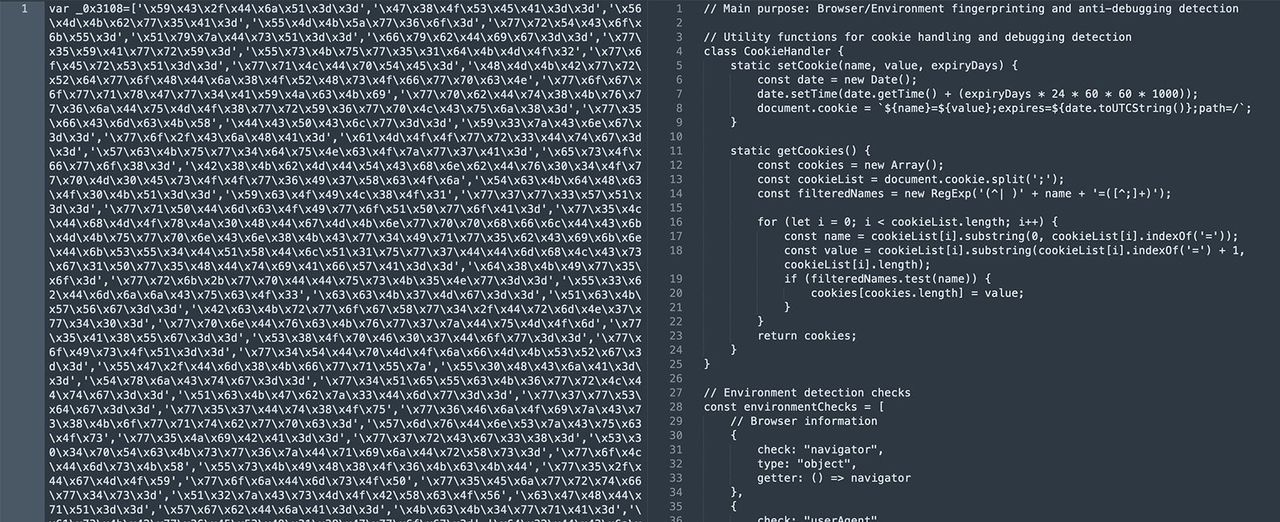
Through this analysis, we discovered that the script performs extensive environment checks and stores results in Base64-encoded cookies. This understanding led to the development of more effective handling strategies in our rebrowser-patches library.
Triggering the Security Check
For testing purposes, you can deliberately trigger the security check using this code:
await page.evaluateOnNewDocument(() => {
window._Selenium_IDE_Recorder = 1
})
This sets one of the automation detection flags, forcing the security system to display the challenge page.
Solving the Challenge
Using our rebrowser-patches library, the process of solving the hCaptcha challenge involves:
- Accessing the iframe containing the challenge
- Extracting the required parameters:
- websiteURL
- websiteKey
- User-Agent string
- Proxy information (if applicable)
- Obtaining the solution token (gRecaptchaResponse)
- Submitting the solution
hCaptcha regularly updates its challenge datasets, making automated solving increasingly complex. While AI solutions exist, human-powered solving services often provide more reliable results.
Automatic Detection and Solving
Key Feature: All our cloud browsers fully support automatic detection and solving of Imperva security checks, typically completing the process in under 10 seconds.
The automatic solving process involves:
- Real-time detection of Imperva security challenges
- Automatic handling of hCaptcha frames
- Seamless token generation and submission
- Cookie management for subsequent requests
This automation capability eliminates the need for manual intervention in most cases, making it ideal for:
- High-volume automated workflows
- Continuous data collection processes
- Systems requiring uninterrupted operation
- Scalable web automation solutions
Legal Considerations
When interacting with Imperva-protected websites, keep in mind:
- Web scraping of publicly accessible data is generally legal worldwide
- The scraping process must not harm or overload the website
- Always comply with the website's terms of service
- Consider using caching services when available
Conclusion
Understanding Imperva's security mechanisms is crucial for developing effective and compliant automation solutions. Our open-source rebrowser-patches library provides the tools needed to handle these challenges properly while maintaining undetectability.
For more detailed information about handling CAPTCHAs and security challenges, please refer to our documentation.