TCP vs UDP: Understanding the Differences and Use Cases
TLDR: Key Takeaways
- TCP is connection-oriented and ensures reliable, ordered data delivery, while UDP is connectionless and prioritizes speed over reliability.
- TCP is ideal for applications requiring data integrity, such as web browsing and file transfers, while UDP is better for real-time applications like gaming and streaming.
- The choice between TCP and UDP depends on the specific requirements of your application, considering factors like speed, reliability, and data integrity.

Introduction to TCP and UDP
In the world of computer networking, two protocols stand out as the workhorses of data transmission: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). These protocols, both part of the Internet Protocol suite, play crucial roles in how data is sent and received across networks. Understanding the differences between TCP vs UDP is essential for anyone involved in network engineering, software development, or IT infrastructure management.
This comprehensive guide will delve into the intricacies of TCP and UDP, exploring their characteristics, advantages, disadvantages, and ideal use cases. By the end of this article, you'll have a clear understanding of when to use each protocol and how they impact network performance.
What is TCP?
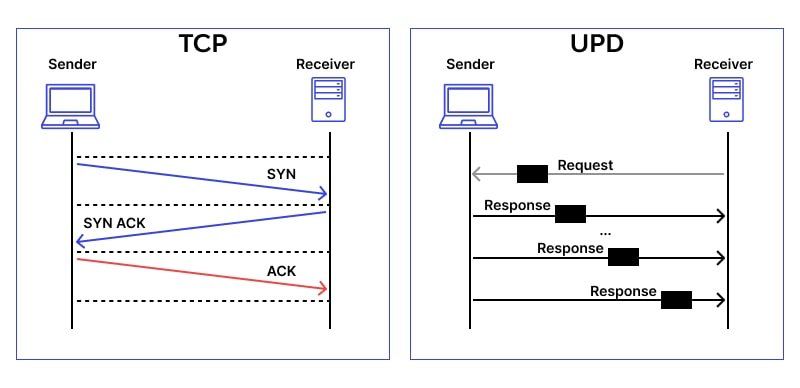
Transmission Control Protocol (TCP) is a connection-oriented protocol that provides reliable, ordered, and error-checked delivery of data between applications running on hosts communicating over an IP network. TCP is one of the core protocols of the Internet Protocol suite and is widely used for many popular applications.
Key Features of TCP
- Connection-oriented: TCP establishes a connection before data transfer begins.
- Reliability: TCP ensures that all data packets are delivered in the correct order.
- Flow control: TCP manages the rate of data transmission to prevent overwhelming the receiver.
- Congestion control: TCP adjusts its transmission rate based on network congestion.
- Error detection and correction: TCP uses checksums and acknowledgments to ensure data integrity.
Advantages of TCP
- Guaranteed delivery of data packets
- Ordered delivery of data
- Robust error checking and correction mechanisms
- Flow control to prevent overwhelming receivers
- Congestion control to optimize network performance
Disadvantages of TCP
- Higher overhead due to connection establishment and maintenance
- Slower transmission speeds compared to UDP
- Not suitable for real-time applications with low latency requirements
- Increased network resource usage
- Potential for "head-of-line blocking" in some scenarios
Common Use Cases for TCP
TCP is ideal for applications that require reliable and ordered data delivery. Some common use cases include:
- Web browsing (HTTP/HTTPS)
- Email (SMTP, IMAP, POP3)
- File transfers (FTP, SFTP)
- Remote administration (SSH)
- Database connections
What is UDP?
User Datagram Protocol (UDP) is a connectionless protocol that provides a simple, unreliable transport layer for sending data packets between applications. Unlike TCP, UDP does not establish a connection before sending data and does not guarantee delivery or ordering of packets.
Key Features of UDP
- Connectionless: UDP does not establish a connection before sending data.
- Unreliable: UDP does not guarantee packet delivery or ordering.
- Low overhead: UDP has minimal header information and processing requirements.
- Fast transmission: UDP can send data quickly without waiting for acknowledgments.
- Support for broadcasting and multicasting: UDP can send packets to multiple recipients simultaneously.
Advantages of UDP
- Lower latency due to no connection establishment
- Faster data transmission compared to TCP
- Reduced overhead and network resource usage
- Suitable for real-time applications
- Support for broadcasting and multicasting
Disadvantages of UDP
- No guarantee of packet delivery or ordering
- Lack of flow control and congestion control mechanisms
- Limited error checking compared to TCP
- Potential for packet loss in congested networks
- Application-layer responsibility for handling reliability if needed
Common Use Cases for UDP
UDP is well-suited for applications that prioritize speed over reliability. Some common use cases include:
- Online gaming
- Voice over IP (VoIP)
- Live video streaming
- DNS queries
- IoT device communication
TCP vs UDP: Key Differences
To better understand the distinctions between TCP and UDP, let's compare them across several key aspects:
| Aspect | TCP | UDP |
|---|---|---|
| Connection | Connection-oriented | Connectionless |
| Reliability | Guaranteed delivery | No delivery guarantee |
| Ordering | Ordered packet delivery | No packet ordering |
| Speed | Slower due to overhead | Faster transmission |
| Header size | 20-60 bytes | 8 bytes |
Choosing Between TCP and UDP
When deciding whether to use TCP or UDP for your application, consider the following factors:
- Data integrity requirements: If your application cannot tolerate any data loss or out-of-order packets, TCP is the better choice.
- Speed and latency: For applications that prioritize low latency and fast data transmission, UDP may be more suitable.
- Network conditions: In networks with high packet loss or unreliable connections, TCP's reliability features can be beneficial.
- Application type: Real-time applications often favor UDP, while applications requiring guaranteed delivery typically use TCP.
- Resource constraints: UDP's lower overhead may be preferable in resource-limited environments.
TCP and UDP in VPN Applications
When it comes to VPN (Virtual Private Network) applications, both TCP and UDP have their roles to play. Many VPN providers, including those offering mobile proxy services, support both protocols. Here's how they're typically used:
- OpenVPN over UDP: This is often the default configuration for many VPN services. It provides a good balance of security and speed, making it suitable for most general-purpose VPN usage.
- OpenVPN over TCP: This configuration is sometimes used when UDP is blocked or unstable. It can be more reliable in certain network conditions but may be slower than UDP.
For users looking to optimize their VPN performance, especially when using services like mobile proxies, it's crucial to choose a high-quality provider that offers both TCP and UDP options. This flexibility allows users to select the protocol that best suits their specific needs and network conditions.
Conclusion
Understanding the differences between TCP and UDP is crucial for making informed decisions about network protocols in various applications. While TCP offers reliability and ordered delivery at the cost of higher latency, UDP provides speed and lower overhead at the expense of guaranteed delivery.
The choice between TCP and UDP ultimately depends on the specific requirements of your application. By carefully considering factors such as data integrity needs, speed requirements, and network conditions, you can select the protocol that best suits your use case.
As networking technologies continue to evolve, it's essential to stay informed about the latest developments in protocol optimization and emerging alternatives. By doing so, you'll be well-equipped to make the best choices for your networking needs, whether you're developing applications, managing network infrastructure, or simply trying to optimize your internet connection.
Frequently Asked Questions
Which protocol is faster, TCP or UDP?
UDP is generally faster than TCP. This is because UDP doesn't establish a connection or wait for acknowledgments before sending data, resulting in lower latency and quicker transmission speeds.
Can I use both TCP and UDP in the same application?
Yes, it's possible to use both TCP and UDP in the same application. Many applications use TCP for reliable data transfer and UDP for time-sensitive operations that can tolerate some data loss.
Is UDP less secure than TCP?
UDP itself is not inherently less secure than TCP, but it provides fewer built-in security features. Security in UDP-based applications often needs to be implemented at the application layer. For sensitive data transmission, additional security measures should be applied regardless of the protocol used.
Why is TCP used for web browsing instead of UDP?
TCP is used for web browsing because it ensures reliable and ordered delivery of data packets. This is crucial for correctly loading web pages, as all elements need to be received in the right order and without loss to display properly. TCP's error-checking and retransmission capabilities make it ideal for this purpose.
How do TCP and UDP affect VPN performance?
TCP-based VPNs tend to be more reliable but potentially slower due to the overhead of establishing connections and acknowledging packets. UDP-based VPNs are generally faster and work better for real-time applications, but may be less stable in poor network conditions. Many VPN providers offer both options to cater to different user needs.





